十大禁止安装应用入口概述
不少用户在使用智能手机时,难免会遇到各种各样的应用程序。然而,并不是所有的应用都值得安装。许多软件可能存在安全隐患、侵犯隐私或违反法律法规的问题。因此,了解哪些是被禁止安装的应用,是保护个人信息和设备安全的重要一步。
一、恶意软件与病毒
某些流行的软件因其隐藏功能而成为了恶意软件。这类程序通常伪装成正常应用,一旦下载后便开始窃取数据或者感染系统。例如,各类“破解”工具往往包含潜伏的病毒,会对手机造成严重损害。同时,也有一些看似无害但实际上暗藏木马程序的软件,它们通过获取权限来监控用户行为或盗取敏感信息。
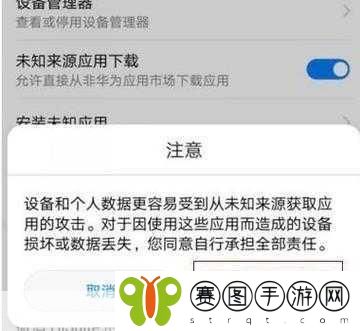
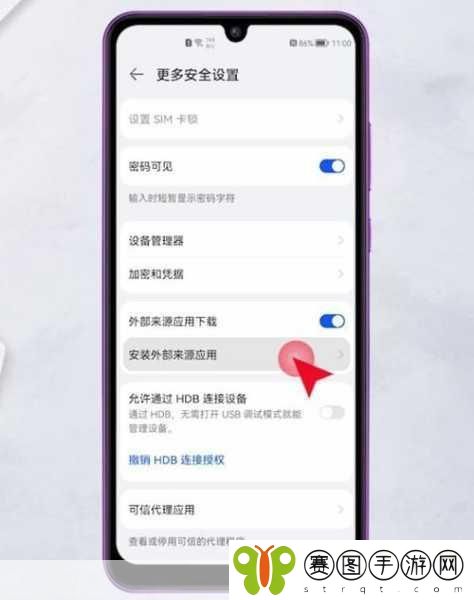
二、不受信任来源
在非官方渠道下载应用常常导致不必要的风险。一些第三方市场没有严格审核机制,使得大量未经验证甚至非法开发的软件进入平台。即使这些软件声称能提供独特功能,但其背后的潜在危害不可小觑。在选择下载源时,要确保它们具有良好的信誉并受到广泛认可。
三、侵犯隐私权的应用
Certain apps request excessive permissions that are not relevant to their functionality, raising red flags about privacy violations. Applications like some social媒体平台可以要求访问联系人、摄像头及位置等敏感信息,而实际用途却与之无关。在进行任何下载前,应仔细阅读相关权限请求,以避免将私人资料暴露于不当用途下。
四、高风险金融服务App
A range of financial-related applications频繁出现在黑名单上,因为它们可能涉及欺诈行为,包括虚假的投资机会或借贷服务。这些APP看起来十分正规,但很容易让人陷入金钱骗局,因此建议谨慎处理此类内容,通过官方网站或者已知渠道进行操作以降低风险。








